Since Chrome will never interrupt your browsing experience to prompt you to update by default, it’s clear that you’re dealing with a PUP or browser hijacker if you get this message while browsing the Internet using Google Chrome.
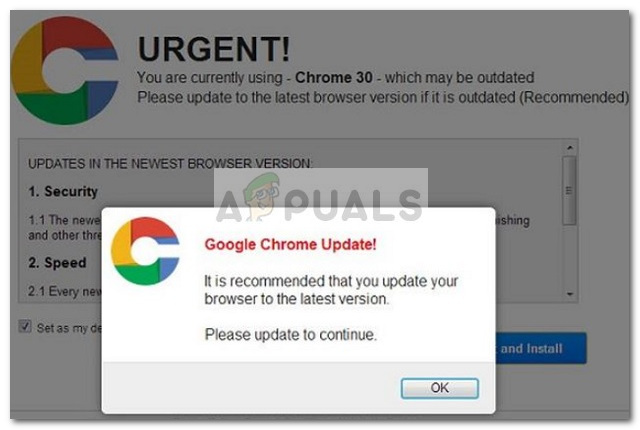
Keep in mind that this malware is different from the Urgent Chrome Update Pop-up Scam and needs to be removed in a different way.
How the Critical Chrome Update Scam works
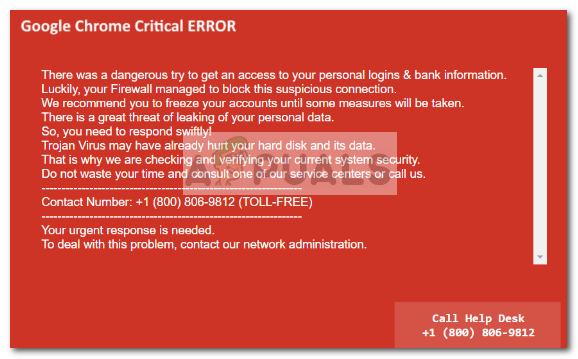
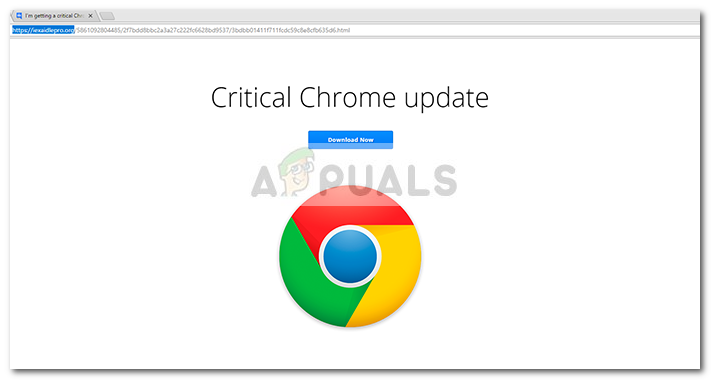
The Critical Chrome Update scam is one of the newest social engineering techniques created to deliver harmful code to an unsuspected user. The end goal is to convince the user to click the Download Now button. This will trigger the download of a self-extracting BAT file that most likely contains a web browser toolbar, an “optimization utility” or another type of product that will end up generating pay-per-click revenue to the adware publisher. However, there is a more serious possibility where the Download Now button will trigger the download of spyware of file-encrypting ransomware. Security reports on this particular malware scam have reported the following domains as hosts:
iexaidlepro.orgjohphblogger-hints-and-tips.orgtahxiintimes-niedersachsen.org
Note: These are just the most popular occurrences. Since the network of these pages is fast-flux, the domain names keep changing in an attempt to avoid blackmailing mechanisms and antimalware suites. Furthermore, the actual URL will contain a long tail of random-looking characters. Design-wise, the landing page with the large logo and the genuine-looking Download Now button is identical to Chrome’s Download Page. The scam is definitely an improvement to the rudimentary Chrome Update Pop Up Scam.
The scam is powered by a PUP
The apparition of this scam tab is not scripted by any action that the user has to take. The malware page is programmed to appear in the middle of the user’s browsing session in order to make it look genuine. A PUP is a type of malicious software capable of infecting a computer without the permission of the user. In this particular case, the PUP that is causing this malicious behavior most likely arrived by an extremely popular method called bundling. Bundling is the act of hiding malicious code or redirect in a third-party installation client. Since most 3rd party programs used are freeware available on popular download sites, users will usually just hit the Next button without unchecking the installation of bundled software. Once the PUP arrives safely on the victim’s computer, it will start hijacking the Chrome browser in order to create redirects that will steer the user towards clicking the Download Now button that will download the actual virus.
How to Remove the Critical Chrome Update Scam virus
If you’re currently dealing with the Critical Chrome Update Scam, there is some good news – by following a set of instructions, you’ll manage to contain and even eradicate the infection quite easily. Of course, it will be much easier to deal with the Critical Chrome Update Scam if you didn’t click the Download Now button and allowed the infection to spread. If you are getting frequent scam pop-ups, there are a few steps that you can follow to stop the Critical Chrome Update Scam pop-ups from interfering with your browsing sessions: the automatic way and the manual way. Below you have a collection of steps that will enable you to eliminate the infection completely. Note: If you want to ensure that the infection has been dealt with completely, do not skip any of the steps presented below. Since some malware programs have restorative properties, you might end up dealing with the issue all over again in a few weeks if you don’t remove it completely.
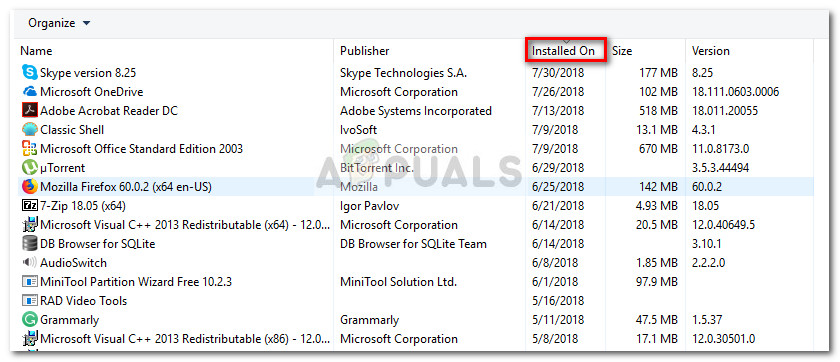
Step 1: Uninstalling the PUP program from your computer
In this first step, we are going to try and locate the Potentially Unwanted Program that was used to deliver the malicious code. I know it might seem hard to figure out which program is responsible, but the process is quite easy if you know where to look. By looking at the Programs and Features menu and uninstalling every entry that is not accounted for you will eventually take care of the culprit. To make it easier for you, we created a step by step guide along with a list of potential culprits: Once every potential culprit has been uninstalled, move down to Step 2.
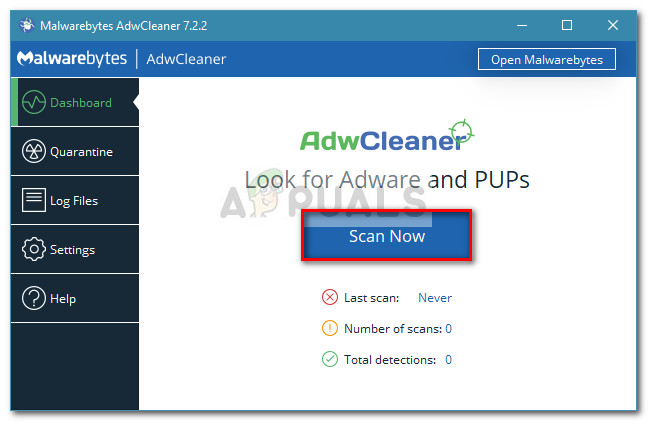
Step 2: Removing any Adware with AdwCleaner
Now that we previously dealt with the program that delivered the infection, let’s remove any leftover adware code with a specialized program. There are a number of programs that will allow you to do this, but we recommend AdwCleaner. This Malwarebytes developed product is a free utility that the vast majority of users affected by the Critical Chrome Update Scam have successfully used to resolve the issue. Here’s a quick guide on using AdwCleaner to scan your PC and remove any leftover adware code of the Critical Chrome Update scam: At the next startup, you should no longer be prompted by the Critical Chrome update tab. But just to be sure you remove every last bit of malicious code, move down to Step 3.
Step 3: Performing a system-wide malware scan
Now that the source of the infection and the leftover malware code has been dealt with, it’s the time recommended to use a powerful on-demand scanner that will look beyond PUPs. There are a lot of dedicated security scanners to choose from, but we recommend a full Malwarebytes scan for the best results. If you’re not that computer savvy, you can follow our step-by-step guide (here) on downloading, installing, and using Malwarebytes to remove any other types of infections. Once you successfully manage to run a scan with a powerful on-demand security scanner, move down to Step 4.
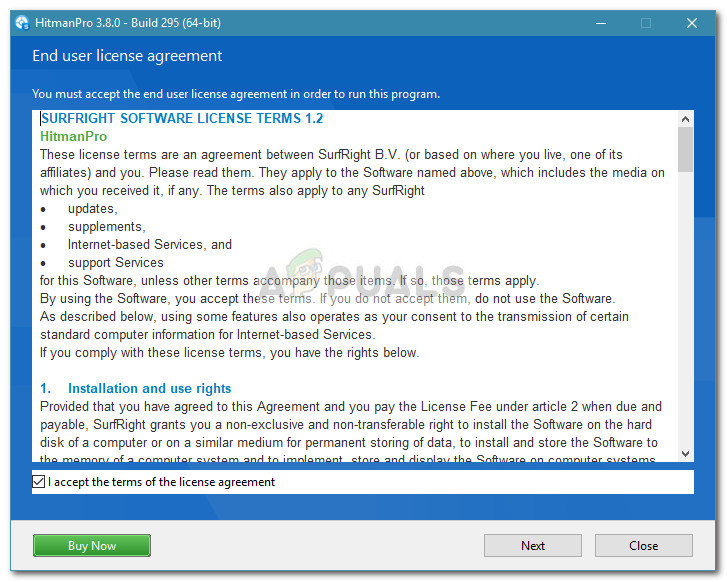
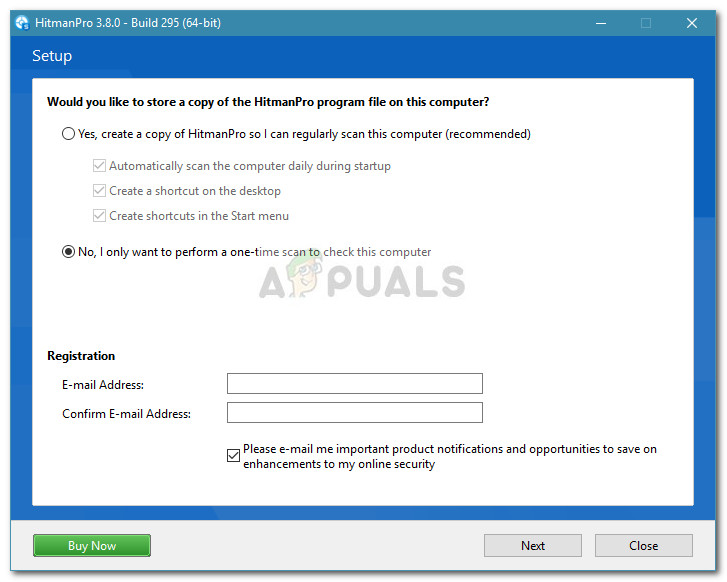
Step 4: Double-checking with HitmanPro
By now, your system is probably free of infection and the Critical Chrome Update Scam pop-ups should no longer occur. However, since some types of infections will leave your system vulnerable to other malware threats, it’s better to double-check than to feel sorry later on. HitmanPro is a malware scanner that is extremely efficient in identifying and dealing with riskware. Most security researchers recommend a HitmanPro scan right after a regular antivirus scan to make sure that the antivirus suite didn’t miss anything. Here’s a quick guide on how to download, install, and run a HitmanPro scan:
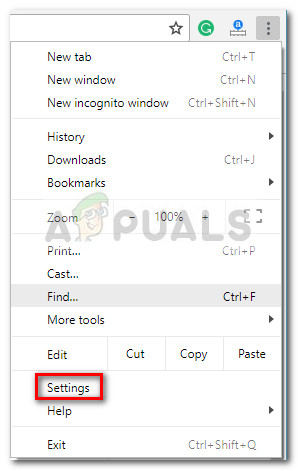
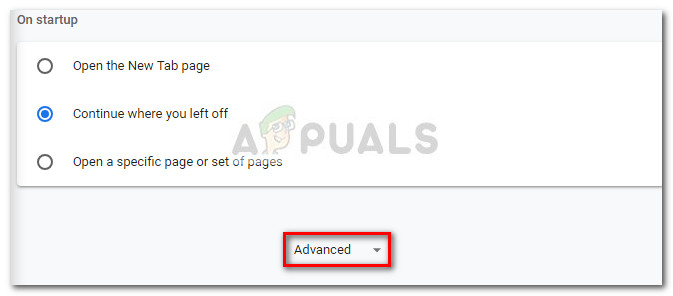
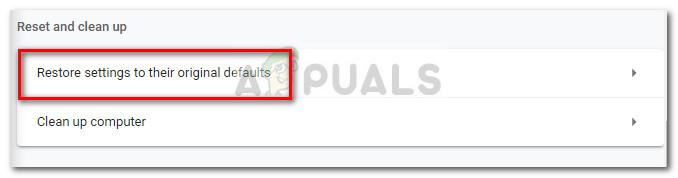
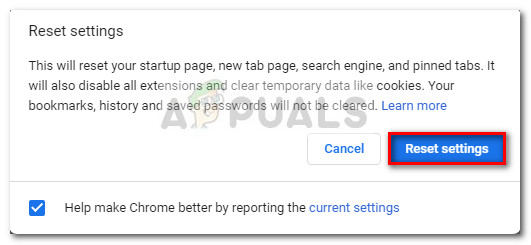
Step 5: Reset Chrome browser to default settings
If you’ve come this far, you’ve only got one more thing to do before you can safely say that your system is free of the Critical Chrome Update Scam. To ensure that you don’t have any leftover malicious code capable of hijacking your Chrome browser, it’s important to reset it’s settings to the defaults. Here’s a quick guide on how to do this:
Last Free Update For Windows 7 Released, KB4534310 And KB45343140 Are The Final…An Analysis of the IRS Phone Call Scam: What to Expect in 2019How to Remove the “Debug Malware Error 895-System32.exe Failure” Scam AdwareMSI Accused of Scalping 3080 Cards on Ebay: Scam Seller Disguises Himself Ever…